Permissioned Blockchain - Step to Create
Today everything and anything is twisted into the hands of the users. And when we say blockchain the very first thing coming to mind is transparency and decentralization. If it's told a permissioned space can provide both - is that convincing? A Permissioned blockchain Network can bend your needs to act, operate with decentralized qualities and yet be transparent with its customized access. Get to know about the Permissioned blockchain and its benefits. And catch up on how to Create a Permissioned Blockchain.
What Is A Permissioned Blockchain?
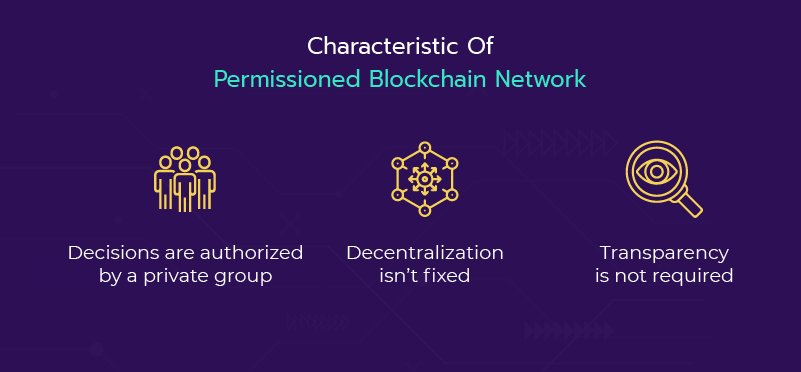
A limited access network comprising users and nodes - Permissioned Blockchain that task a strong leap in the market today. With permission users who are layered with security and safety, they ensure the quality of decentralization is withheld. The network tracks the user's transactions and administers them. The data access controls are very much convenient to use and customizable for our requirements. Moreover, most enterprises, with multiple operating systems, and supply chains prefer this network as it is beneficial. They secure the data and also take control of the cover. Here to join the network, it's not the same as open blockchain. The owner has to be permitted to enter and similarly, the functions are also restricted based on requirements. One can create a permissioned network based on the requirement of the entrepreneur or the operator.
Basics To Create Permissioned Blockchain Network
It is important to analyze the need and define the functions of the network you are creating. Based on your business niche and its requirements, analyze formulating the do and don'ts needed. Market standards and competitor analysis help in understanding how business performances have shifted with time and space.
There are multiple blockchain networks. Choosing the right one to set up your permissioned network will be the next step. Every blockchain network has its quality and nature. Based on the operations, functioning, and need, choose the right network. Also, check on its interoperability.
Now go ahead designing the permission set of your network. Set every possibility in and work out on building the permissioned architecture of your network. You can customize your permission for the Operators and operations carried out.
Head in the development phase. Choose the right developer. And ensure your codes are authorized and are of audit quality. Your developer must efficiently provide the deliverables on time, with custom functions, and also fit in the budget. BlockchainX facilitates the best results in development, our hands-on experience in creating permissioned networks has helped businesses meet market standards.
Test and check for errors even after the launch. Check and keep giving updates which are mandatory to stand and survive in the space.
Step-By-Step Guide On Permissioned Blockchain Creation
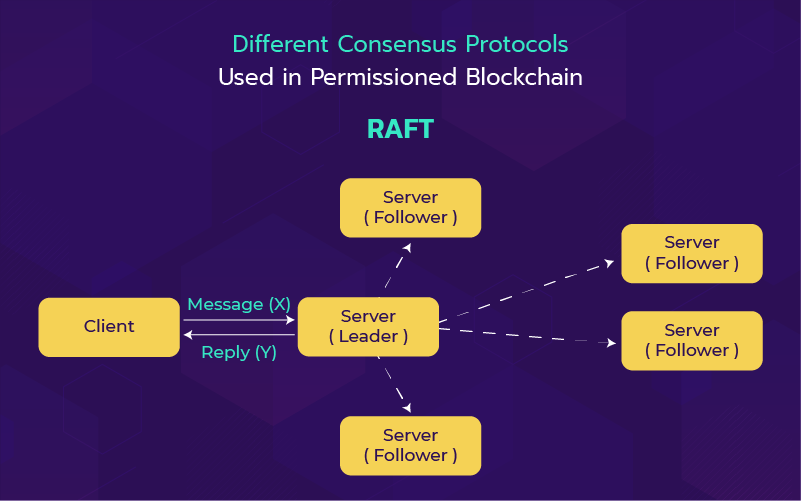
Here a basic detailing of how to create a permission blockchain is explained with Subtate through a node authorization pallet. This allows the operation of configured groups of nodes using node authorization pallets in the network. This prebuilt Frame pallet uses peer identification to identify each node and the account owner is only allowed to claim the node.
To approve a node in the network, you can follow any of the two methods.
1. As a part of the network's genesis setup, bring the peer identifier into the chain specification file list of Pre Configured nodes. This method requires the chain governance mechanism’s permission or access to the SUDO pallet root account on the network.
2. One can ask a particular node to get paired as a peer connection. A node's private or public key can be used to generate peer identifiers and that's used in the time of connecting between the nodes.
Configure Rust and Rust toolchain when creating your permissioned blockchain with the substrate.
The very first step is to build the node template of the chain. Based on the background research and the requirements the template is fixed.
When adding a new pallet it should carry a little information to configure files for the compiler to create the runtime before use. These configuration parameters and dependencies have control over the final binary compilations. Hence few crucial information is demanded.
To stimulate governance the pallet is set to use the EnsureRootpriviledge function also called the Sudo pallet. To mention node templates come with Sudo Pallets itself and they allow making calls from the root level administrative management. The production setting has more realistic governance checks.
The Rust trait of Config is present in all pallets that determine the presence of parameters and type requirements of the pallet. A pallet-specific code requires pallet implementation using the trait. Pallet-specific codes need to be added to the pallet.
Before getting launched into the network, the per identifier along with account identifiers extract further details from the authorized node. And the approved nodes link to the predetermined account.
The nodes check for compliance after changes are made in code, when no syntax error reflexes, they are good to go!
The subkey allows for generating and inspecting your key and inspecting other keys connected to the account. By using the subkey generate-node-key command the peer identifier and node key will be produced randomly.
The permissioned network will be launched and the nodes allowed can join using node key and peer identifiers. Here in the case of 4 nodes, the first three nodes can be set permission to author and validate the blocks while the fourth can be the subnode that can only extract certain data with the consent of the node owner.
Essential Keys Required To Submit Transaction
The key account can be for signing in and submitting transactions based on the other node’s impact on the behavior. While submitting or signing in a transaction impacting the node you don't own
The transaction must be chain data for reference
The signature key with the necessary origin must be accessible in the Keystore.
To develop an account every node has a signing key. Using the account to act on behalf of the node, it's possible to sign and submit transactions impacting any connected node. The operators would require node keys in case of creating a permissioned network for their real-time business operations. And the node owner account helps in signing and submitting transactions with the node where it has central control of the signature key.
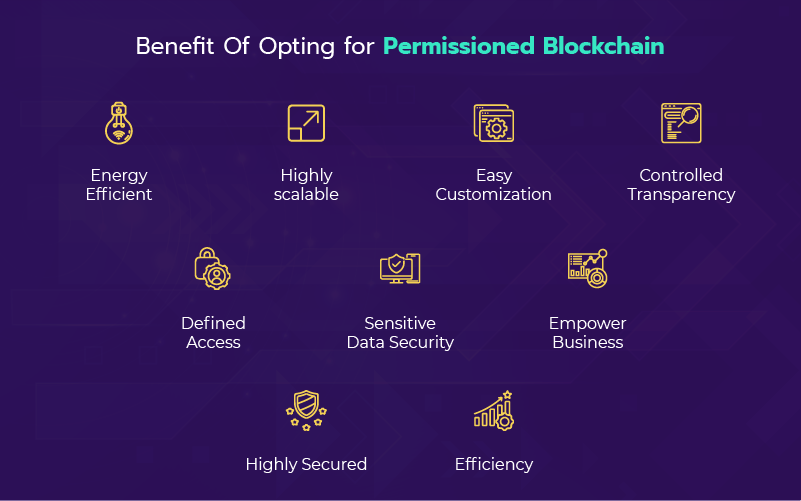
Benefits Of Permissioned Blockchain
When we have to choose to develop a network for a business, the Permissioned blockchain and its benefits are comparatively high and effective in multiple means. With node operation restrictions the network functions with good speed, and transactions happen effortlessly and efficiently. The consensus mechanism streams the process in the permissioned network with a sizable node count.
Moreover, customizing permissioned blockchain is an added advantage that helps in specifying tasks effectively and is also easy to modify and adapt for the need. The transparency in the network is controlled and based on the degree of access the nodes are permissioned to perform.
Next, the access is central and controlled by node authorities. A permission blockchain is more secure where the data is open to only those who require it. Controlled permission and access play a vital role in minimizing energy usage. Transactions are validated with a pre-selected number of nodes.
By offering a safe and open platform to perform business activities through a strict yet not so constrained, a permission blockchain is your right choice. They facilitate the targeted and specialized perceptions and streamline better in gaining results. As they intend to offer sturdy security limiting access to authorized users you build a trustworthy network. Providing a balanced transparency system helps in constructing the best solution for the business and its operations.
Create Your Permissioned Blockchain Network
With extended security and customized transparency, these networks contribute in a better way. Creating a permissioned blockchain network for your business shall help you in all the functioning. From management to monitoring, regulations operations, and functions everything is done and jotted in with simple permissions. BlockchainX over the years, we have trained, skilled, and experienced craftsmen to curate your demanded network. We can help you customize your requirements into the form you demand.





